Using the right technology can streamline operations, enhance customer engagement, and boost overall productivity. Despite its potential benefits, many small businesses often make significant mistakes when it comes to technology implementation. Let’s explore some of the biggest technology blunders small businesses make and how to avoid them.
SCW Blog
Data is commonly regarded as one of a business’ most valuable resources. As such, it is critical that you protect it from threats of all kinds, including data leaks. Data leaks are nothing to take lightly, as their impacts range from a serious hit to your business’ reputation to an equally serious hit to your business’ finances. Obviously, this is something to be avoided, so let’s discuss how you can do so.
Today’s business leans on collaboration more than ever. Employees that work together efficiently and effectively can streamline processes and create a lot of positive momentum for a business that includes enhancing productivity and fostering innovation. Let’s go through a few variables that fuel solid collaboration.
We’ve all found ourselves in a pickle due to a dead smartphone battery, and if not, you’ve been living with a charger perpetually on your person. What is it that kills a smartphone’s battery so quickly?
As it turns out, a lot of things impact your smartphone’s capability to hold and maintain a charge over time. Let’s run through the list of factors that you could encounter, and how you can address them.
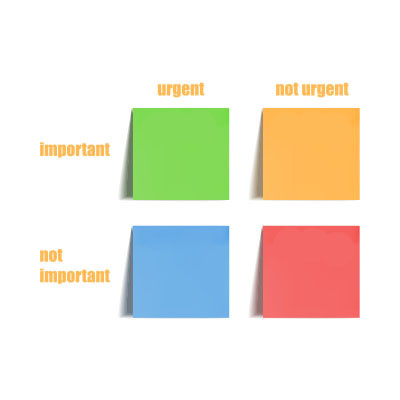
The modern worker has a lot of challenges and one of them is a laundry list of tasks to accomplish. For this reason, it’s best to have a plan for tackling your to-do list. One of the most effective ways to prioritize tasks is through what is called the Eisenhower Matrix. Inspired by a speech given by the former President of the United States and the Supreme Commander of the Allied Expeditionary Force in World War II, the Eisenhower Matrix simplifies complex task lists to make getting through them more effective. Let’s take a look at how it works.
The IT infrastructure of any business can be complicated, especially if you’re going about things the right way. In fact, managing your technology is, more often than not, a full-time job that needs to be fulfilled in order to be done appropriately. Let’s go over some of the key parts of managing and maintaining a business IT infrastructure, and while we cover these tasks, ask yourself if you’re 100% confident that they are happening for your business.
Look, we know that thinking about disasters can be a nerve-wracking experience, but you need to acknowledge that your organization is constantly in danger of becoming subverted by challenges outside your control. While you might not be able to stop a disaster from striking, you can be prepared for when it does strike, as well as how you respond to it. Let’s go over some of the methods you can use to ensure you have a plan in place.
For the growing business, doing the right things to secure your network and data is a constantly evolving situation. For larger businesses, they tend to approach the situation with a different perspective. They plan out the whole process. This is what is called enterprise security. Let’s take a look at what enterprise security entails and how the little guy can benefit from doing things like larger companies do them.
Cybersecurity has never been more important. There are millions of scams sent out every day that are ultimately targeting you and your employees’ password-secured accounts. Today, we are going to give you some tips on how to create passwords that work best to protect your data and information systems.
Phishing is a word that has a couple of different meanings, depending on the spelling and context. Fishing, like the act of sitting down with a pole and trying to catch a fish, can be a relaxing, leisurely activity. Phishing, with a “ph,” is anything but that, and it can be a tiring and scary situation to navigate—particularly if you or one of your employees have fallen victim to an attack.
Admit it, you don’t know all that much about cybersecurity. In this blog, we spend a lot of time discussing security issues. After all, today there are more threats than ever and many different types of problems that IT administrators, business decision-makers, and even individual employees have to deal with. Over the next two weeks, we have decided to discuss the reality of cybersecurity and what you need to know to get out in front of it.
It’s not uncommon for an employee to hold a second job outside of your office, whether it’s a side gig that they are trying to turn into a passion project or a side hustle just to make ends meet or put away a little extra money every month. Workers holding multiple jobs is certainly not unheard of—if anything it’s more common than ever, thanks to the remote work surge. How does this phenomenon impact your organization?
Cybersecurity, to many, can sound inherently complicated—complicated enough, perhaps, that many may elect to put it off for as long as they can, or even choose to go without it. Even without our obvious bias factoring into our considerations, this is a bad idea. Let’s go over some basic security practices that are simple to enact, but can easily make a world of difference for your security.
The cloud can be a tricky beast to tame for your business, and it is mostly because of all the options you have at your fingertips to help your organization be as successful as possible with it. Let’s discuss some of the questions you need to ask to ensure you get the best value out of your cloud-based solutions.
Smartphones are a critical part of your business’ productivity, but sometimes you and your employees might have differing views on how to translate that productivity into profitability for your business. If you want to avoid the pitfalls associated with smartphones, well, today’s article might just be for you. Here are four tips and tricks you can use to get your smartphones to work for you.
Standing desks have become quite popular, especially as people grow more health-conscious post-pandemic. These desks are a little on the pricey side, so you might be wondering if they are really worth the investment. Can the benefits make implementation worthwhile for standing desks? The answer might surprise you.
Cybersecurity is anything but a new concept, and if recent and current events are any indication, the concept isn’t going anywhere anytime soon. Let’s take a few moments to consider some of the bigger threats currently out there, and how they will influence the threats we see going forward from here.
While we all like to think we are paragons of productivity, the reality of the matter is that it’s far too easy to become distracted while trying to get work done. How do you stay focused when there are so many distractions out there? It all starts with controlling your environment and changing the way you approach these distractions.